Presenting you my first video collaboration with my peers!!
(Ws, 2014)
Prior to undertaking the module Living and Working on the Web, my knowledge of managing my employability through the use of the web was limited. I didn’t use twitter account often, I had never had a blog and I didn’t have a LinkedIn profile. Now, my personal online presence has improved greatly over the course of this module, as my development on this module is quite clearly evident in my self-test!
One of my largest developments will be my Twitter account. Prior to this module, I had never considered how a ‘professional’ twitter would be of use to me. I have really enjoyed interacting with my peers, being able to use hashtags to find (and be found) by people who are interested in similar topics to me, and keeping up to date with businesses and areas which interest me. I was elated to know my Topic 5 post on Open Access was featured by Richard Poynder an independent journalist and blogger specialising in information technology, scholarly communication, open access and open science. Thus increasing my Blog readers and follower on Twitter.
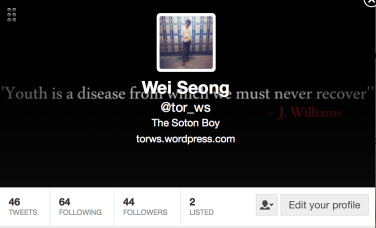

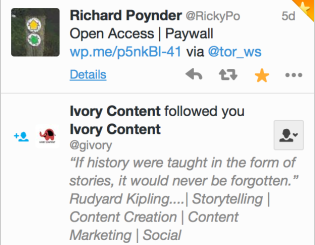
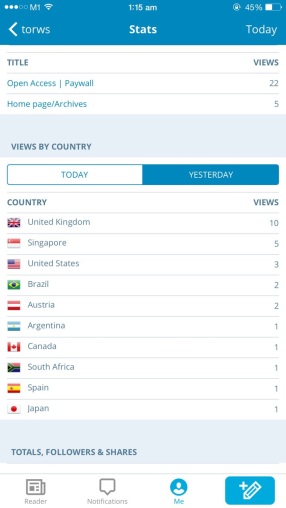
(Evidence of my active use of Twitter)
Following that, I went on to create a linkedIn profile to increase my online presence in the marketing world. Constantly updating my profile and connecting to various influencers and groups has allow me to achieve a profile strength of ‘Expert’. I am attempting to reach out to my previous employee for recommendations to contribute to my profile authenticity.
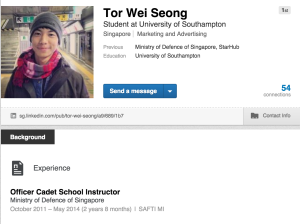
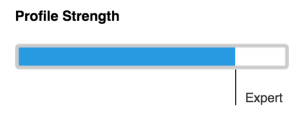
(Example from my LinkedIn)
I have also come to understand the importance in building and authentic profile. Coming up with plans to sync all my online profiles (Social and professional) together in create a single identity in near future. Creating an authentic profile means I will have to be more careful with what I will be uploading and posting in future having understand the potential problem I will face such as ethical issue.
Lastly, to wrap it up. I believed the peer-learning element of the course has greatly aided my learning throughout the five topics we have covered on the course. Similarly outside school context, this could achieve by connecting and interacting with more people online in the same field of study and interest. Therefore, it is important to remember the importance to actively reach out to more people and partaking in discussion to build on our knowledge and network. This module certainly help me to feel more confidence in landing an internship offer by June :))
Want to stay connected with me? Why not? See the footer at the top of my blog? You can find various icon that will navigate you to the rest of my professional accounts!!
(Word Count: 450)
Reference
ws, T. (2014). Final Presentation Mang2049. [online] Youtube.com. Available at: https://www.youtube.com/watch?v=jm0hLuD6Gzg [Accessed 16 Dec. 2014].